An in-depth look into how Arista’s Cognitive Wi-Fi alleviates the burden of network administrators. How it ensures that the Wi-Fi network provides flawless experience to Wi-Fi users using a variety of tools including AI/ML.
Arista Cognitive Unified Wired/Wireless
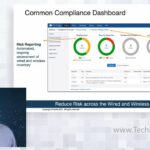
Arista delivers unified Wired and Wi-Fi networks for campus deployments, with a focus on management, operations, the analytics plane, and how these integrations aid a consistent deployment and troubleshooting. IT enables automation of day to day tasks and relieves the network administrator from day to day mundane activates.
Arista Cognitive Campus Vision with Ed Chapman
This session will serve as an introduction to Arista’s Cognitive Wi-Fi Strategy and a brief Arista product portfolio description.
Aruba 630 Series Campus Access Points – Wi-Fi 6E In Action
Watch Aruba’s 6E AP deliver maximum capacity with ultra tri-band filtering to eliminate interference.
Aruba AIOps – Next-Gen Problem Solving and Optimization
Built-in Day 0 to Day N tools to automatically find and fix issues for a better user experience.
Work From Anywhere with Aruba ESP
See how Aruba ESP makes it easy for IT to provide secure connectivity to remote and mobile workers.
Aruba Company Introduction and Update with David Hughes
David Hughes gives an update on Aruba and how their Edge Services platform is helping transform user experience with networking and wireless.
Cisco HyperFlex 5.0 and Intersight: Simplifying Hybrid Cloud Operations
In this session, Cisco deep dives into the latest feature release including Enterprise storage, data security, and predictive automation enhancements. You’ll learn how this new release enables new workloads, eliminates management touch points, and drives greater focus on usability.
Cisco UCS X-Series: UN/Box the Future
Cisco UCS X-Series is the first x86 system exclusively designed for the age of hybrid cloud and the coming decade of industry innovation in computing. In this session, Cisco deep dives into the X-Series architecture, components, and platform details.
Cisco Identity Services Engine (ISE) in AWS with Ansible Automation
ISE 3.1 will be available as a native Amazon Machine Image (AMI) and will help customers use automation tools to provision their deployments whether on-premises, using cloud providers, or hybrid. This session demonstrates how you can use the new cisco.ise Ansible modules to generate configurations from existing deployments and begin to incorporate them into their […]
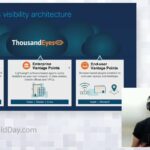
New ThousandEyes Integrations with Cisco Networking Platforms
ThousandEyes now integrates with Cisco SD-WAN router platforms and Nexus 9000 switches, providing customers with scalable, turnkey ThousandEyes vantage points. This session will look at how ThousandEyes Internet and Cloud Intelligence extends Cisco SD-WAN visibility with hop-by-hop network path and app performance insight.
Cisco Future Cloud Overview with Prashanth Shenoy
Prashanth Shenoy, Vice President of Product Marketing for Enterprise Networking and Cloud, gives an overview of the newest announcements made in Future Cloud.