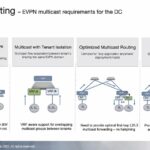
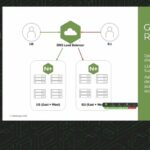
This video is a focused look at Arista’s role in routing, and how EVPN is evolving within the data center and the MPLS backbone for next-generation VPN services.
Arista Networks DANZ Monitoring Fabric
Get the latest on Arista’s innovations for pervasive Network Observability, with a focus on the DANZ Monitoring Fabric.
Arista Networks CloudVision as-a-Service
In this video, get an overview of Arista’s new CloudVision SaaS platform, bringing cloud tools to the Enterprise transforming network operations, monitoring and support.
Arista Networks Technology Updates with Ken Duda
Ken Duda highlights of key technology investment areas for Arista and gives an overview of the philosophy behind their decisions and strategy going forward.
What’s New at Arista Networks with Doug Gourlay
Get Arista’s perspective of the networking industry today and learn what they have been working toward with recent acquisitions across the networking and security space.
IP Fabric Insights Demo with Pavel Bykov
In this video, we find out more about how IP Fabric does what it does, the information it gathers and how we can start querying it, both in tables and through visualisation. Then we delve into the compliance reporting capabilities of IP Fabric. With the depth of data in the platform, we can report on […]
IP Fabric Company Introduction
IP Fabric is billed as an Automated Network Assurance Platform. In this segment, after introducing themselves, our speakers will walk through the challenges they have seen and how IP Fabric has developed to provide solutions to those problems.
Monitor a Web App with F5 Beacon
Åsa Persson, Regional Sales Directir, discusses how to monitor a web application using F5 Beacon. She is joined by Adil Laari, Product Manager, who give an overview of the capabilities of F5 Beacon: App monitoring, user experience monitoring, and actionable insights. Finally, Forrest Crenshaw gives a demonstration of F5 Beacon in action with the space […]
Make Your Web App Resilient with F5 DNS Cloud Service
Rick Salsa, Product Manager, continues the NGINX Sprint 2020 space app demo by deploying a global DNS cloud service. The F5 DNS Cloud Service includes DNS Load Balancer which can distribute server load across multiple instances. During and after this demo, James takes questions from the Tech Field Day delegates.
Add an API with NGINX Controller API Management
Liam Crilly, Director of Product Management, continues the NGINX Spring 2020 space app demo by publishing the app API for other consumers. He uses NGINX Controller, an API lifecycle management solution for NGINX Plus. During and after this demo, Liam takes questions from the Tech Field Day delegates.
Secure a Web App with NGINX App Protect
Daniel Edgar, Project Manager, continues the NGINX Sprint 2020 Space App demo by adding a web application firewall, NGINX App Protect. This high-performance, lightweight WAF is a dynamic model integrated with NGINX Plus. During and after this demo, Daniel takes questions from the Tech Field Day delegates.
Improve Performance with NGINX Plus
James Jones, Solutions Architect, continues the NGINX Sprint 2020 web app demo with a focus on improved performance. James adds an NGINX Plus load balancer with microcching to reduce the impact on the Unit server. He also adds the ability for Promethius to access metrics from the environment. During and after this demo, James takes […]
Deploy a Web App on NGINX Unit
Libby Meren, OSS Product Marketing Manager, and Timo Stark, Professional Services Engineer, demonstrate how NGINX Unit can be used to deploy a dynamic application. In this first demonstration from NGINX Sprint 2020, Timo and Libby build a gallery of planets in a Docker container. The container includes NGINX Unit and WordPress alongside a skeleton API […]