Meter Platform Demo: Deploying Meter End-to-End
Meter provides internet infrastructure for the enterprise. This hands-on session, led by Meter Co-founder and CTO, Sunil Varanasi, brings Meter’s product to life. With a live demonstration of bringing a network up from 0 to 1, Sunil will show you how Meter’s vertically integrated stack delivers immediate results. This demo will showcase Meter’s end-to-end solution […]
Meter Architecture Overview with Sunil Varanasi
Meter provides internet infrastructure for the enterprise. In this session, Meter Co-founder and CTO, Sunil Varanasi will take you under the hood of Meter’s architecture, showcasing the complete stack—from hardware to software. He’ll dive into how Meter’s Network Operating System powers its entire stack, enabling rapid product innovation. This talk examines how Meter’s network architecture […]
What is Meter? Building from the Ground Up
Meter provides internet infrastructure for the enterprise. In this session, Meter Co-founder and CEO, Anil Varanasi explores the “why” behind Meter and what makes Meter different. You’ll leave with an understanding of how Meter works, Meter’s ambitions, and why we believe it will be the last networking company.
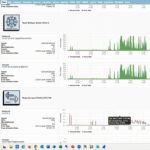
PathSolutions TotalView Operational Demo
See a demo of PathSolutions TotalView and how it can speed troubleshooting for help desk employees. This demo discusses how the platform can conceptualize errors quickly and give you actionable information to solve these issues and reduce time spent on trouble tickets.
How PathSolutions Brings Advanced Network Monitoring with Automated Network Troubleshooting to Enterprises
Automating network troubleshooting is something that other network monitoring systems can’t offer because they don’t collect enough information and don’t have any analytical capabilities to help solve problems. PathSolutions TotalView provides Total Network Visibility® meaning that you will know more about your network than with any other monitoring system.
Productize Your Network Automations with Itential
Orchestrating the provisioning of infrastructure is a key opportunity to capture and store essential data throughout the deployment process. Every time you automate provisioning, you can gather critical insights—technical details, product states, and more. However, without proper tracking and organization, it becomes challenging to understand what’s running where, its current state, or the next steps […]
Using Itential to Orchestrate Your Network Automations
Most network teams leverage some sort of domain-specific automation, whether through open-source tools or controller-based software to implement network changes more efficiently. While automating individual tasks may suffice in certain cases, scaling infrastructure as a product for broader consumption requires standardized processes. Orchestration unifies tools, services, and automations across your ecosystem, streamlining each step for […]
Operationalize Your Network Automations with Itential
You’ve built a library of useful automations to automate tedious, time-consuming tasks. But as your efforts scale, so do your headaches. You’ve got different scripts for different tasks, written in different languages, with varying levels of access. And when your network starts to grow (along with the complexity of what you need to automate), things […]
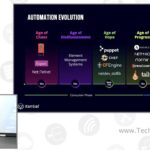
Itential and The Evolution of Network Automation
Network automation is going through an evolution right now. Most network engineers have built awesome scripts or playbooks that solve some problems but you’re nowhere near deploying like AWS. For most, automation likely saves you some time and reduces human error but isn’t the sort of thing you can package up into a product and […]
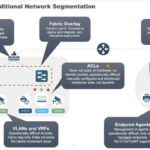
Elisity Microsegmentation Platform Demo – Clinical Healthcare Use Cases
This Elisity presentation at Network Field Day 36 focuses on includes the Elisity Microsegmentation Platform Demo: Securing Clinical Healthcare Networks with Identity-based microsegmentation platform that accelerates an organizations Zero Trust maturity. Watch this comprehensive demo of how Elisity’s cloud-native microsegmentation platform transforms security for clinical healthcare environments. In this video, we showcase how leading healthcare […]
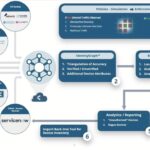
How to Optimize a Microsegmentation Architecture with Elisity
This Elisity presentation at Network Field Day 36 focuses on how Elisity’s microsegmentation architecture leverages a cloud-native distributed control plane that separates policy management from enforcement. At its core, the system utilizes a centralized policy management platform that integrates with existing identity providers and maintains the Elisity IdentityGraph—a comprehensive mapping of all network assets, their […]
Elisity Top Microsegmentation Challenges and Goals Across the Manufacturing Pharmaceutical and Healthcare Industries
This Elisity presentation at Network Field Day 36 focuses on how the convergence of IT and OT networks has created unique cybersecurity challenges across manufacturing, pharmaceutical, and healthcare sectors, where legacy systems, unmanaged devices, and critical operations intersect. This technical talk explores how microsegmentation addresses the distinct security requirements of these regulated industries. In manufacturing […]
Elisity Microsegmentation Platform Origin Story
This Elisity presentation at Network Field Day 36 includes an overview of the Elisity origin story. Elisity was founded in 2019 and has was built to be a leap forward in network segmentation architecture and today Elisity is leading the enterprise effort to achieve Zero Trust maturity, proactively prevent security risks, and reduce network complexity. […]
Accelerate Zero Trust Maturity Through Enterprise-Wide Microsegmentation with Elisity
Elisity empowers enterprises to rapidly improve their security posture and accelerate Zero Trust maturity across their entire digital ecosystem. Our revolutionary approach to microsegmentation delivers comprehensive protection for all users and devices—across IT and IoT/OT—without disruption or complexity. The Elisity IdentityGraph automatically discovers and correlates your complete network landscape, providing the contextual intelligence needed to […]
Arista CloudVision 360 Network Observability
Also Part of the CloudVision Update, Praful will share a demo of the latest CloudVision capabilities for the Data Center. Arista’s CloudVision dramatically simplifies operations with automation, observability and zero trust security capabilities across all enterprise networking domains, from campus to data center, WAN, and cloud.
Arista CloudVision Campus Demo with Paul Druce
As part of the CloudVision Update, Paul will share a demo of the latest CloudVision capabilities for the Enterprise campus networks. This uniform approach helps enterprises save operational expenses by removing traditional network operational silos while delivering reliable and resilient networks.
Arista CloudVision for the Multi-Domain Enterprise
Arista’s CloudVision dramatically simplifies operations with automation, observability and zero trust security capabilities across all enterprise networking domains, from campus to data center, WAN, and cloud. This uniform approach helps enterprises save operational expenses by removing traditional network operational silos while delivering reliable and resilient networks. This CloudVision Update session will be a retrospective on […]