Infinidat, a company founded in 2011 with deep roots in enterprise storage, has established itself as a critical player in the IT storage infrastructure for some of the world’s largest companies. The company’s founder, who previously created EMC Symmetrix and sold XIV to IBM, has leveraged this extensive experience to build Infinidat into a provider […]
Streamline AI Projects with Infrastructure Abstraction from HPE
In this presentation, Alex Ollman from Hewlett Packard Enterprise (HPE) discusses the transformative potential of infrastructure abstraction in accelerating AI projects. The focus is on HPE’s Private Cloud AI, a solution designed to simplify the management of complex systems, thereby allowing data engineers, scientists, and machine learning engineers to concentrate on developing and refining AI […]
Building a Generative AI Foundation with HPE
Join Hewlett Packard Enterprise’s product team for a deep dive into the AI architecture and infrastructure needed to deploy generative AI at enterprise scale. We’ll explore the essential components—from high-performance compute and storage to orchestration—that power these models. Using real-world case studies, we’ll uncover the intricacies of balancing computational resources, networking, and optimization. Discover how […]
A Step-by-Step Guide to Build Robust AI with Hewlett Packard Enterprise
Generative AI holds the promise of transformative advancements, but its development requires careful planning and execution. Hewlett Packard Enterprise (HPE) leverages its extensive experience to navigate the intricacies of building enterprise-grade generative AI, covering aspects from infrastructure and data management to model deployment. Alexander Ollman, a product manager at HPE, emphasizes the importance of integrating […]
Managing Google Cloud Storage at Scale with Gemini
In the presentation, Manjul Sahay from Google Cloud discusses the challenges and solutions for managing vast amounts of data in Google Cloud Storage, particularly for enterprises involved in data-intensive activities like autonomous driving and drug discovery. He highlights that traditional methods of data management become ineffective when dealing with billions of objects and petabytes of […]
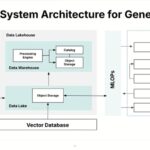
Google Cloud Vertex Al & Google Cloud NetApp Volumes
Rajendraprasad Hosamani from Google Cloud Storage presented on the integration of Google Cloud Vertex AI with Google Cloud NetApp Volumes, emphasizing the importance of grounding AI agents in bespoke, enterprise-specific data. He highlighted that AI workloads are diverse and that agents can significantly enhance user experiences by providing interactive, personalized, and efficient data sharing. For […]
Google Cloud Storage for AI ML Workloads
In his presentation on Google Cloud Storage for AI ML workloads, Dave Stiver, Group Product Manager at Google Cloud, discussed the critical role of cloud storage in the AI data pipeline, particularly focusing on training, checkpoints, and inference. He emphasized the importance of time to serve for machine learning developers, highlighting that while scalability and […]
Workload and AI-Optimized Infrastructure from Google Cloud
Sean Derrington from Google Cloud’s storage group presented on the company’s efforts to optimize AI and workload infrastructure, focusing on the needs of large-scale customers. Google Cloud has been working on a comprehensive system, referred to as the AI hypercomputer, which integrates hardware and software to help customers efficiently manage their AI tasks. The hardware […]
A Demonstration of the MinIO Enterprise Object Store – The AI-Centric Feature Set
MinIO’s AI feature set is expansive, but there are core features that allow enterprises to operate at exascale. Those include observability, security, performance, search and manageability. In this segment, MinIO goes from bucket creation to RAG-deployment, emphasizing each core AI feature and why it matters to enterprises with data scale challenges that run from PBs […]
Why MinIO is Winning the Private Cloud AI Battle
Many of the largest private cloud AI deployments run on MinIO and most of the AI ecosystem is integrated or built on MinIO, from Anyscale to Zilliz. In this segment, MinIO explains the features and capabilities that make it the leader in high-performance storage for AI. Those include customer case studies, the DataPod reference architecture […]
Why AI is All About Object Storage with MinIO
Almost every major LLM is trained on an object store. Why is that? The answer lies in the unique properties of a modern object store – performance (throughput and IOPS), scale and simplicity. In this segment, MinIO details how AI scale is stressing traditional technologies and why object storage is the de facto storage standard […]
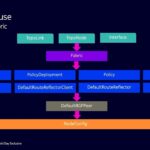
Rethinking Data Center Infrastructure Automation with Nokia – Operations Made Easy
Bruce Wallis, Senior PLM on the Event Driven Automation (EDA) solution shifts gears to explain the operational capabilities of the data center fabric with a focus on the state of the network and the way that EDA abstractions reduce the complexity of the day to day tasks for data center operations teams.
Rethinking Data Center Infrastructure Automation with Nokia – Fabric Creation
Bruce Wallis, Senior PLM on the Event Driven Automation (EDA) solution delves deeper into how EDA automates the key deployments steps of setting up a new data center fabric, including the creation of an underlay network (the fabric) and overlay services (EVPN) via the power of the EDA app-store.
Rethinking Data Center Infrastructure Automation with Nokia – EDA Overview
Bruce Wallis, Senior PLM on the Event Driven Automation (EDA) solution explains the thinking behind the EDA infrastructure automation engine and the core foundation of the solution for data center networks.
The Path Towards Consumable Network Automation with Nokia
Network automation has been talked about for over 10 years, yet the adoption of automation tools within the enterprise network is sporadic, with many only deploying islands of automation. Nokia IP Head of Technology and Architecture and Bell Labs Fellow, Wim Henderickx will discuss what needs to change to make the network more consumable. Through […]
Nokia for IP Networking with Vach Kompella
In a rapidly evolving tech landscape, Nokia has emerged as a formidable player in global IP networking, captivating the attention of technical engineers worldwide. Nokia is not just keeping pace with the demands of modern networking but is also setting new standards. Hear from Vach Kompella, the leader of the Nokia IP team on how […]
Nokia for the Data Center and Beyond
Industry veteran Michael Bushong has recently joined the Nokia team to lead business development for IP solutions into the data center. What piqued Mikes interest in what Nokia was building and ultimately drove him to join? Mike will cover his view from the outside and provide insights into Nokia and the key differentiations that sets […]
Infinidat Presents at AI Data Infrastructure Field Day 1
Infinidat provides enterprise storage solutions for the world’s most demanding businesses. We are the critical IT storage infrastructure of the world’s biggest companies for their mission critical applications and workloads, which include databases, ERP systems, virtual infrastructure and now critical AI workloads, such as Retrieval Augmented Generation (RAG). We offer high performance file and block based storage solutions, to fit your […]