Automating Day 1 to Day N Operations with NodeWeaver
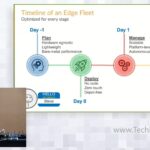
We continue the “hero’s journey” to focus on addressing the real world operational challenges from day 1 going forward. Here we will discuss and demonstrate cluster expansion, failover, automated management, autoscaling, remote management, application deployment, and service chaining. We will also discuss the unique security challenges presented by the distributed edge and how NodeWeaver addresses […]
Automating Day -1 to Day 0 Operations with NodeWeaver
We will take you through a “hero’s journey” of the real world challenges associated with deploying, managing, and operating edge compute infrastructure from day -1 through day N. In this section, Tom and Lorenzo will focus on day -1 to day 0 and provide a live demo of NodeWeaver’s zero-touch provisioning and configuration capability while […]
NodeWeaver Platform Overview
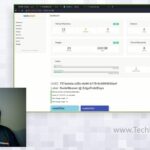
Carlo will provide a high-level overview of NodeWeaver’s key features and functionality and demonstrate these capabilities via the UI. This will also provide additional context for the other demos. NodeWeaver is an advanced platform that enables extensive control over a NanoCloud through both web browser and API-based interfaces. Key features include hiding hardware properties, enabling […]
Tackling Edge Computing Challenges with NodeWeaver
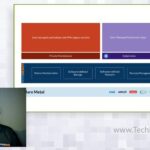
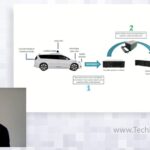
There are many unique challenges associated with deploying, managing, and operating compute infrastructure for running applications at the distributed edge. In this presentation, NodeWeaver CEO Carlo Daffara discusses these challenges and outlines key NodeWeaver customer use cases. NodeWeaver is an innovative software layer specifically designed to navigate the complexities of edge computing. By transforming hardware […]
Demo of HPE MicroServer and StorMagic SvSAN Failure Scenarios
In this video you’ll see a live demonstration of how SvSAN keeps applications running, even when servers fail. We show a simple, 2 node solution with 2 HPE MicroServers and the witness running on a Raspberry Pi. The demo shows the VMs continuing to run even when one server and the witness have their power […]
Demo of HPE MicroServer StorMagic SvSAN Deployment
In this video you’ll watch a live demonstration of a StorMagic SvSAN VSA being installed on HPE MicroServers in a VMware environment. The video will show the tools used and the simplicity of the process.
HPE ProLiant MicroServer Gen10 Plus v2 Product Overview
In this video, Tim Daron, HP’s Solutions Architect for SMB and mid-market solutions, introduces the MicroServer Gen 10 Plus V2. Powered by the Intel Xeon E Series, this compact server prioritizes security with features like Silicon Root of Trust for firmware authentication. Tim highlights its ILO version five and mentions its resemblance to the DL […]
StorMagic and HPE Showcase Edge Solutions
Strategic partners since 2020, HPE and StorMagic are joining forces at Edge Field Day 2 to show how HPE servers with StorMagic SvSAN virtual SAN software are an ideal solution to help customers solve all of their problems at the edge. The joint platform’s simplicity, flexibility and low cost make it an ideal choice for […]
The Value of High Density Storage at the Edge with StorageReview and Solidigm
Addressing the ever growing edge storage market is no easy task. Jordan Ranous, a Technology Analyst at StorageReview shares how a variety of workloads and customers like Cheetah RAID are benefit greatly from Solidigm’s High Density QLC SSD solutions. In this session you will dive in deep on how and why these workloads operate more […]
The Value of Solidigm SSDs Delivered at the Edge
Want to understand how Solidigm SSDs are the best options for today’s most demanding read-intensive workloads? Tahmid Rahman, Data Center Director of Product for Marketing at Solidigm will how the Solidigm SSD portfolio tackles AI and edge workload in a variety of storage systems. Solid-state drives (SSDs) have evolved significantly over the years, showcasing developments […]
The Value of Solidigm Form Factors at the Edge
Not all edge servers are created equally. Depending on the workload, application or system configuration, there’s a need for high density storage that is available in a variety of form factors to fulfill the needs of a multitude of edge servers on the market. Jeniece Wnorowski, Influencer Marketing Strategist, shares the latest and greatest Enterprise […]
The Edge Storage Landscape and Edge Storage Challenges with Solidigm
As workloads evolve at the edge and become more read and data intensive, there is a need for a variety of high density storage solutions. Roger Corell, Solutions Marketing Director at Solidigm, shares how he and his team are helping organizations implement so of some of the most efficient and highly scalable storage solutions on […]
Fortinet Presents at Cloud Field Day 18
Full App Lifecycle Security through Distributed, AI-driven, Cloud Automation In this session Fortinet will demonstrate how the modern cloud SOC scales and supports advanced workflows through the practical use case of advanced automation. The scenario will be formatted as a red team/blue team engagement where AI-driven automation reduces risk dwell time and multiple points of […]