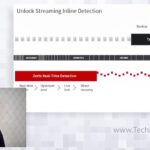
With the new release of Zerto 10 comes added functionality for you to achieve ransomware resilience with Zerto real time encryption detection built into the Continuous data protection ensures the earliest warning sign that ransomware may be impacting your virtual environment. Using the Zerto unique journal organizations can now be even more confident with rapid […]
Terraform Orchestration Bare Metal Demo via RackN Digital Rebar API
Demonstration of declarative APIs in RackN Digital Rebar that make it easy to automate pools of bare metal infrastructure using IaC orchestrators like Terraform to empower developers with available, reliable and fast self service. In this RackN demo section, the focus is on showing a Terraform demo for orchestration. The scenario involves an enterprise trying […]
Generative DevOps Powering the 10x Operator with RackN and Backstage
Demos declarative APIs in RackN Digital Rebar that make it easy to automate clusters of bare metal infrastructure using Dev Portals like Backstage.io to empower developers with available, reliable and fast self-service. In this conversation, Rob and Shane discuss their roles as developers and the integration of Backstage and Digital Rebar. Rob explains that he […]
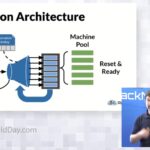
Empowering Platform Engineering with RackN Infrastructure Platform
RackN Digital Rebar Infrastructure Platform provides the available, reliable and fast automation needed by operations teams to support enterprise Platform Engineering efforts. RackN focuses on infrastructure platforms and platform engineering, addressing challenges faced by operations teams through their self-managed software called Digital Rebar. Their goal is to empower companies to independently manage their infrastructure, whether […]
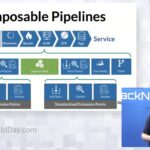
Morpheus Data Workflows: Scaling Automation and IaC via Self-Service
Going beyond developer self-service and provisioning of application instances, this session will spotlight how Morpheus can be used to help IT simplify operations and scale GitOps style automation initiatives. By decoupling the creation and execution of automation scripts and infrastructure-as-code patterns, organizations can streamline and govern the use of technologies like Terraform, Ansible, Puppet, PowerShell, […]
Morpheus Data Plugins: Extensibility for Hybrid Cloud Platform Operations
For years, Morpheus has led the hybrid cloud management market when it comes to rapid integration of third-party technologies with dozens of out-of-the-box codeless integrations into clouds, ITSM, IPAM, Backups. This session goes deep on the underlying service delivery framework within Morpheus and showcases how third-party plugins can be developed to expose data for custom […]
Morpheus Foundation: Developer Self-Service and Platform Operations
This demo and deep dive will illustrate how enterprises and service providers can enable DevOps speed and agility while also improving control and reducing cost of delivering IT services. We’ll show how easy it is to integrating technologies like VMware, Nutanix, AWS, Azure, GCP, ServiceNow, Terraform, Ansible, and more while providing a governance framework and […]
Morpheus Data 101: The Rise of Hybrid Cloud Platform Operations
For years, Morpheus has led the hybrid cloud management market when it comes to rapid integration of third-party technologies with dozens of out-of-the-box codeless integrations into clouds, ITSM, IPAM, Backups. This session goes deep on the underlying service delivery framework within Morpheus and showcases how third-party plugins can be developed to expose data for custom […]
Roots to Cloud: Cisco Wireless Legacy and Vision
The Meraki and Catalyst brands come together to unite Cisco Wireless Solutions built on lessons learned from millions of deployed networks across the globe. The new Unified Cisco Wireless Solutions are transforming the Enterprise supporting the most demanding use cases with ease of deployment, configuration and management through intuitive centralized platforms that offer on premises […]
NetAlly CyberScope Product Walkthrough and Demo
In Part 2 of NetAlly’s presentation to #MFD9, James Kahkoska (CTO) covers the benefits and techniques to perform an onsite security assessment by demonstrating the use of CyberScope, NetAlly’s new cyber security analyzer, a handheld instrument that provides unprecedented visibility to expose possible site security concerns and interior threats.
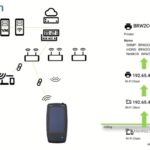
Enabling Wi-Fi Site Assessments with NetAlly CyberScope
In Part 1 of NetAlly’s presentation to #MFD9, James Kahkoska (CTO) – in his classic Field Day storytelling style – talks about the history of innovation, mobility, and the evolving complexity of site networks – and the impact of this complexity on cyber security. He relates how common network analysis capabilities can be utilized for […]
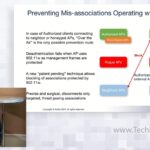
What’s Cooking in WIPS with Arista
A viable WIPS offering needs to constantly adapt to mitigate new threats. In this section we will introduce a number of innovations that enable automatic detection and prevention of threats related to newer standards and practices such as; WPA3, OWE, 802.11w, client MAC randomization.
Arista Cognitive Campus Unified Wired + Wireless Architecture
In this session, we will discuss how we are building a truly unified wired + wireless architecture for campus networks that is based on open standards, and also discuss large enterprise reference network designs.
Arista AIOps in Action: Proactive Root Cause Analysis
In this session, we will do a quick recap of the core AIOps functionalities built into our CloudVision platform and share some of the new features including Automated Root Cause analysis, that we have been working on to make the life of network admins easier.