This session discusses innovations of the converged Wi-Fi AP going beyond this with IoT, IoT services and additional edge services built from using containers to perform functions for various types of XaaS. There will be demo examples of use cases and services with IoT solutions.
Ruckus Cloud Service with Practical Artificial Intelligence for Networks
This session will show how RUCKUS is leveraging AI/ML analytics to address network challenges, discussion of various uses cases, review key features such as incidents, anomalies, etc. that benefit IT staff and a demonstration of the solution.
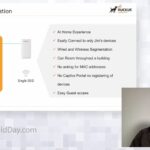
Simplifying Large Shared Networks With Ruckus and Network Segmentation
This session addresses how users and devices of all kind can onboard securely with Identity based policies for access, network personalization through easy to use management portals and the ability to roam throughout a variety of environments. It will also cover deployment and design flexibility of such a solution at scale along with management and […]
Juniper and the Policy of the Future
With the proliferation of atypical devices connecting to enterprise networks today, customers are facing increased policy complexity and device security concerns, and existing NAC solutions aren’t keeping up. Juniper is reshaping this landscape with our own take on addressing these complexities. Come hear about our strategy and vision for policy, onboarding, and self-provisioning.
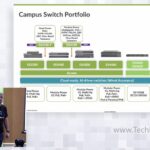
EXpect the UnEXpected with Juniper
The EX4100 is the latest addition to the Juniper’s EX Switching portfolio, bringing performance, bandwidth, port density and other key features to a variety of enterprise campus and branch environments. Like the previously launched EX4400, the EX4100 is optimized for simplicity and scale with native cloud-based operations, and it enables the best user and IT […]
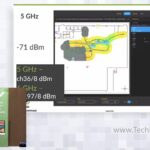
Juniper AI-Driven Enterprise: Wireless
Good Wi-Fi starts with a good Wireless LAN design. That means considering bandwidth requirements, business applications, Wi-Fi 6E, physical environment, RF, RSSI (Signal), SNR (Noise) and all the rest of the alphabet soup. Find out how Juniper AI-Driven Enterprise Networks are built for the future.
Juniper AIOps and Location
As Juniper continues to produce the latest and greatest hardware, our AI and software capabilities continue to gain more features and functionality to solve some of the biggest challenges for IT professionals. The Juniper Mist solution now helps solve some of these challenges by automatically validating the actual placement and orientation of APs post install […]
Juniper and the Marvis Journey
The power of the Marvis conversational assistant is that it can contextualize requests to accelerate troubleshooting workflows, answer product or feature specific questions, provide information about the network, and help find any type of network device. We’ve also added new client and wired insight capabilities to Marvis—the industry’s first and only virtual network assistant driven by Mist AI.
Juniper AI-Driven Enterprise: Momentum and What’s New
Here at Juniper, we strive to deliver network experiences that transform how people connect, work and live. We are the fastest growing wireless vendor. By challenging the inherent complexity in networking, our AI-driven self-driving secure full stack solution powers the connections that matter most – from education to healthcare to secure banking. Our commitment is […]
HPE GreenLake for Disaster Recovery
HPE GreenLake for Disaster Recovery – unlocking the fastest recovery experience in one simple platform, with unlimited scale. Click here to learn more!
Komprise Architecture: Smart Data Workflows Chalk Talk
In this session Komprise CTO Mike Peercy will dig into the Komprise Intelligent Data Management architecture and walk through how Komprise delivers the right data to the right location and teams at the right time. Mike is known for his whiteboard chalk talks. You don’t want to miss this session.