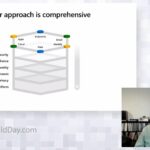
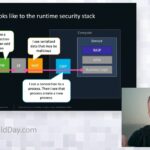
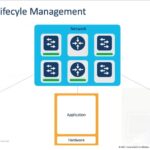
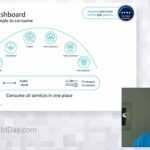
In this demo, we will show you how to overcome supply chain security risks and address ransomware by putting immutable infrastructure principles into action. We will demonstrate how to use SaltStack automation on our out-of-band platform, which we’ll use to build, destroy, and re-build an edge data center — with ease and at scale.
ZPE Introduction: Why Cybersecurity for Enterprise Can’t Be Solved By One Vendor
Cybersecurity vendors are at the top of their game. So why are cyberattacks increasing and becoming more effective? We’ll discuss the modern enterprise’s pain of having too many products, from too many vendors, which leaves too many security gaps. We’ll also discuss why this dynamic attack surface can’t be solved simply by adding more products, […]
Effective Threat Containment with Arista Macro-Segmentation
Segmentation is not a new concept and yet, many organizations struggle to be successful at this key security control due to the implementation complexities. Sachin Vador dives into how Arista’s approach provides a standards-based mechanisms for segmentation while avoiding challenges such as TCAM exhaustion and proprietary formats.
Pervasive Visibility to Deliver Zero Trust with Arista DMF
Visibility is foundational to security, but legacy network packet brokers are broken when dealing with enterprise-wide security threats. Prashant Gandhi will describe how Arista DANZ Monitoring Fabric provides pervasive observability via a modern, programmable monitoring fabric, enabling security analysts and tools with access to any packets/flows at any time in addition to traffic insights.
Arista Awake Labs: Real World Incident Response Case Studies
In this session, Kevin Adams-Romano will share a few examples that illustrate the need for network visibility for effective threat hunting and breach response. The network represents ground truth and with the right combination of people, process and technology, it can offer the early warning signs needed to disrupt attacks ranging from ransomware and insider […]
Detecting Modern Threats with Arista NDR
Networks have become more complex and perimeters have vanished. Yet, we are still reliant on decades-old network security platforms as defenses from modern threat actors. Gary Golomb will discuss the challenges with relying on data sources like NetFlow and present recent innovations in the Arista NDR platform that address those challenges.
Arista Introduction and Security Strategy with Rudolph Araujo
Arista provides visibility, detection and response across wired, wireless, and cloud infrastructure. In this introduction, Rudolph Araujo will talk about Arista’s AI-driven approach to enable the customer’s zero trust journey as well as how the company brings decades of experience to bear for customers through threat research, incident response, and threat hunting solutions.
How to Secure your Secrets with Keeper Security
Since IT network secrets unlock access to highly privileged systems and data, securing secrets is just as critical to preventing cyberattacks as securing end-user passwords. One study found that 75% of ransomware attacks involve compromised credentials – most of the time, RDP credentials. However, secrets management is a challenge for IT teams, who must mitigate […]
Microsoft Security Automate Threat Detection and Response with SIEM+XDR
Today’s threat landscape continues to grow in complexity, sophistication and frequency. As advanced attacks emerge, Microsoft is on the frontlines working with customers and partners. We’ll share the latest technology around our integrated SIEM+XDR solution, to protect your environment end-to-end and get ahead of adversaries.
Microsoft Security Azure Active Directory – Zero Trust
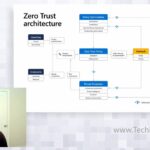
Microsoft defines Zero Trust as a proactive, integrated approach to security across all layers of the digital estate that explicitly and continuously verifies every transaction, asserts least privilege, and relies on intelligence, advanced detection, and real-time response to respond to threats. Nitika Gupta, Principal PM Manager, will cover the lessons we’ve learned across thousands of […]
Microsoft Security Overview with Ryan Mcgee
Microsoft Security is committed to empowering every person and every organization on the planet to achieve more by providing comprehensive protection. It brings together the capabilities of security, compliance, identity, endpoint management, and privacy, designed to work in your multicloud and multi-platform environment. Microsoft Security helps defend organizations around the world against the evolving threat […]
VAST Data Announces Next Generation Platform Concept Called Ceres
An introduction to a next generation platform concept called Ceres. Enabled by VAST’s Universal Storage data platform, Ceres is built leveraging new hardware technologies including NVIDIA BlueField DPUs (data processing units) and Solidigm ruler-based hyperscale flash drives that improves performance, simplifies serviceability and reduces data center costs. Presented by Jeff Denworth, Co-Founder and CMO.
Cisco Secure Application for AppDynamics
Cisco dives into Secure Application, the only solution purpose-built to protect business-critical applications no matter where they run, from the inside out, to maintain speed and uptime, while balancing risk. You’ll learn by leveraging the AppDynamics agent, Secure Application will uniquely bring together business, performance, and security insights to protect your brand against slowdowns and […]
Cisco Cloud Native Application Connectivity and Security Solutions
Businesses are increasingly adopting Cloud Native microservice-based architectures to enable rapid application development with flexibility, stability, portability, and scale. These Cloud Native architectures present new connectivity and security challenges to operators. Learn how Cisco is bringing their extensive experience, expertise, and thought leadership in networking and security to these new architecture domains. In this session, […]
Cisco Secure Cloud Insights, Beyond Just CSPM
This session will dive into identifying, mapping, analyzing, and securing your cyber assets and attack surface with Cisco Secure Cloud Insights. You’ll learn how to gain full visibility into your complex cloud environments to uncover threats, close compliance gaps, and prioritize risk. Cisco dives into how Secure Cloud Insights moves your visibility from just posture […]
Cisco Nexus Dashboard Bolsters Network Visibility with Innovations
Cisco Nexus Dashboard is the solution that IT has been looking for to be able to build, connect and operate hybrid cloud networks rapidly and securely. In this session, you’ll learn more about Cisco’s latest cloud-neutral innovations, tracking end to end flow across service chains real time, how to break down operational silos between network […]