Juniper doesn’t believe in routers as “dumb pipes” but instead that they can be used to detect and stop attacks. Find out how Juniper’s most widely-deployed MX Series router can stop volumetric DDoS attacks and block command-and-control communications to & from malicious servers.
Cover Your Apps with Juniper Cloud Workload Protection
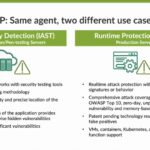
No application is invulnerable to attack, and all applications could use a safety net to help keep them secure, especially in production. Juniper Cloud Workload Protection does exactly that and integrates with the rest of your Zero Trust data center.
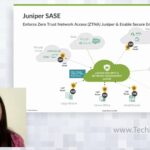
Managing the Transition to SASE with Juniper Security Director Cloud
Manage your security deployments, whether they’re on-premises, in the cloud, or delivered from the cloud as you make your journey towards a SASE architecture.
Juniper Connected Security Overview with Kate Adam
in this video, get introductions to the Juniper team and why Juniper’s Connected Security strategy seeks to make defending the network easier by extending security services to all points of connection from client to workload.
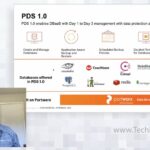
Pure Storage Introduces Portworx Data Services
In this video, Pure Storage introduces their new Portworx Data Services offering, which enables database-as-a-service (DBaaS) with management, data protection, and automation. PDS 1.0 can deploy Cassandra, PostgreSQL, Couchbase, ZooKeeper, Consul, Redis, DataStax, MongoDB, ElasticSearch, Kafka, MySQL, or Microsoft SQL Server simply and quickly. Presented by Goutham Rao, CTO of Portworx.
PathSolutions TotalView Demo with Tim Titus
In this demo, Tim Titus shows an overview of TotalView and how it can be used to help troubleshoot networking issues and provide a root-cause analysis to stakeholders and IT professionals alike.
PathSolutions Solution Overview with Tim Titus
Network troubleshooting usually involves setting your NMS to collect certain data elements, then aligning the clues to the timeframe when the event occurred, and then interpreting the elements to determine what happened. This research is time-consuming and typically requires expert-level understanding of the network. What’s needed is automation of collection, interpretation, and analysis of the […]
Riverbed Troubleshooting Post-Mortem and Conclusion
Phil does a brief troubleshooting post-mortem to review what we’ve done and how Riverbed’s end-to-end visibility solution provides granular and easy network visibility from the client to the cloud.
Diving Deep into Application Performance with Riverbed AppResponse
Vince takes the information we’ve learned so far and uses AppResponse to go deep with looking at transactions between computers and our web servers. He discovers exactly where the problem is located and the root cause of poor performance.
Network Visibility and Synthetic Testing with Riverbed NetIM
Since the application is slow for everyone, including people who don’t have a crypto miner on their computer, Brandon next uses NetIM to look at several key network devices, and he uses our synthetic testing monitoring tools to get some unexpected results.
Investigating a Security Incident with Riverbed NetProfiler
Using NetProfiler, John further investigates our security breach network-wide and learns more about our crypto miner, where it is on the network, and how it’s operating.
Investigating Application Performance at the Client Level with Aternity and Riverbed
Jon starts our troubleshooting session with Aternity to investigate our airport computers, confirm poor application performance, and unexpectedly discover a security breach.
Setting the Stage for End-to-End Visibility with Riverbed
Phil sets the stage for the Riverbed demo scenario and looks at high level application metrics in Portal.