When you choose technology from Intel, you build on open standards, with fully optimized software and security from the hardware up the stack, allowing you to scale-up and out with ease. You are safe in the knowledge that whether you choose to deploy or migrate on-prem, multi-cloud, through communications networks, or on the intelligent edge, […]
Driving Innovation in Cloud Storage with Intel Optane Technology
Disaggregated Cloud Storage is becoming more of the norm in building out additional storage for workloads that rely on larger and larger datasets for data analytics, AI, CDN, and e-commerce. To get the scale efficiencies of storage while maintaining fast performance and dependable latencies that are core to the time to insight, innovation is needed. […]
Protecting Kafka on Kubernetes using Kasten by Veeam
Michael Courcy, Solution Architect for Kasten by Veeam, demonstrates how Kasten K10 can protect Kafka on Kubernetes. First, Courcy discusses the challenges of data management and technical debt in modern applications, and how Kafka can help. But Kafka clusters can be difficult to manage and protect. Kasten K10 is designed to integrate with cloud-native Kubernetes […]
Kasten by Veeam DR Automation with Kubernetes
Michael Courcy, Solutions Architect, demonstrates DR automation for Kubernetes using Kasten by Veeam. In a Red Hat OpenShift container platform, Kasten K10 manages and protects data between multiple datacenter, increasing RTO, decreasing cost, and improving automation.
Cloud-Native Data Protection for Kubernetes: Kasten by Veeam
Tom Manville, Director of Engineering for Kasten by Veeam, presents the philosophy and technology behind their cloud-native data protection for Kubernetes. Kasten K10 was designed to be simple, extensible, and cloud-native, supporting modern DevOps for seamless application transformation and portability. It supports native Kubernetes operators like Vault and provides cloud-native APIs to develop, test, and […]
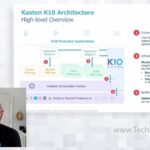
Key Fundamentals of Kasten by Veeam K10
Michael Cade, Senior Global Technologist, presents the “state of the state” for Kasten K10 by Veeam. Kasten K10 is purpose-built for Kubernetes and provides enterprise operations teams an easy-to-use, scalable, and secure systems for backup/recovery, disaster recovery, and mobility of Kubernetes applications. Cade then demonstrates Kasten K10 defeating ransomware using Amazon AWS S3 object storage. […]
Deep Dive on Pliops Technology for Cloud Deployments
Edward Bortnikov, VP of Technology, gives the Field Day delegates a deep dive into Pliops technology for cloud service providers. Database deployments in the cloud require reliability, performance, capacity, and efficiency, and Bortnikov discusses how Pliops was able to bring this to a top SaaS provider, delivering 50% cost savings while increasing reliability and capacity. […]
Responsive and Efficient Storage Architectures for Cloud Service Providers with Pliops
Tony Afshary, Sr. Director Product Line Management, introduces the Pliops solution at Cloud Field Day. After a profile of the company, he introduces the Pliops Storage Processor, providing reliability, performance, capacity, and efficiency for today’s data-centric workloads. Next he discusses how Pliops can be used in disaggregated infrastructure to empower application servers in cloud deployments. […]
Introducing Zerto In-Cloud for AWS EC2 Workloads
For organizations already running many instances, or are actively migrating workloads at scale to Amazon EC2, a new set of challenges are introduced when it comes to disaster recovery in the cloud. In this session, you will hear and see how Zerto is being re-designed to meet the modern demands for resilience in AWS that […]
Protecting Microsoft, Salesforce, and Google Data with Zerto Backup for SaaS
SaaS data is a customer’s responsibility not the vendors, which leaves a customer exposed and at risk when it comes to any type of outage such natural disasters, human error, corruptions, ransomware, or compliance requirements. Zerto’s Backup for SaaS, powered by Keepit, is a new fully automated backup and recovery solution for Microsoft 365, Salesforce, […]
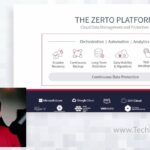
Zerto 9.0 Cloud Data Management and Protection
Through live demos, Gijsbert Janssen van Doorn, Director, Product Management, will showcase Zerto 9 that includes major updates with.new immutability and automation capabilities to further combat ransomware, new advancements with backup capabilities, including new support for additional cloud platforms, new cloud tiering to deliver cost-effective archive storage, and simplified management for both end users and […]
Production-Grade Kubernetes Ingress in a Multi-Cluster World with NGINX
As Kubernetes becomes more prevalent across production environments, the deployment and management of Kubernetes is considered one of the most daunting challenges organizations face when deploying modern apps with exceptional customer experiences. Come and learn more about how NGINX Ingress Controller can help scale, secure, and provide visibility into Kubernetes in production in a multi-cluster […]
Mind the Gap: Connecting Between the Clouds with F5 Volterra
You’ve successfully deployed NGINX in one cloud, but whoops you forget there’s a resource that you need in ANOTHER Cloud! Setup site-to-site IPSEC tunnels? This is OK for a handful of connections, but can quickly spider out of control as the number of your cloud networks increases. In this session Eric Chen, Sr. Solutions Architect, […]
NGINX Edge Security in the Cloud – Turning Bad Actors into Mad Actors
Peter Scheffler, Security Solutions Architect with F5 brings his developer view to securing web applications. Apps are the lifeblood of the internet but they’re also why Bad Actors act badly! Come and learn a little about how bad actors act and some of the ways you can use F5’s App Protect solution within your NGINX […]
Delivering Modern Apps with NGINX
Zubin Tavaria, VP, Marketing gives an introduction and update on NGINX product portfolio, the evolution of modern application architectures, and the role of the NGINX product portfolio in modern apps.
Technical Deep Dive of Hazelcast in the Cloud
The Hazelcast Platform offers many capabilities to run real-time, high-performance applications in public or private cloud environments. Scott McMahon, Technical Director at Hazelcast, will go into technical detail to describe how Hazelcast enables a cloud application strategy.
Hazelcast Cloud Microservices Demo
Neil Stevenson, Platform CTO at Hazelcast, will walk through a demonstration that shows how in-memory data sharing can be implemented in cloud-based microservices to achieve a significant performance boost in a developer-friendly way.
Introduction to Hazelcast Real-Time Intelligent Applications Platform
Hazelcast provides a real-time, intelligent applications platform that powers high-performance IT infrastructures for enterprises that need speed and reliability when seeking insights from their broad range of data sets. Hazelcast senior director of technical solutions, Dale Kim, will give an overview of what the Hazelcast Platform is all about.