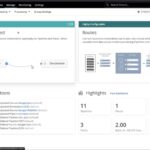
This demonstration explores Cribl Stream and Cribl Edge. Cribl Stream is a vendor-agnostic observability pipeline that gives you the flexibility to collect, reduce, enrich, normalize, and route data from any source to any destination within your existing data infrastructure. You’ll finally achieve full control of your data, empowering you to choose how to treat your […]
Solving Security’s Data Problem with Cribl
Security has a data problem. Despite managing dozens of tools and working closely with IT and external service providers, teams are still struggling to build a sustainable architecture and . We’ll show you how effective use of data pipelines reduces volume, amplifies signal to noise ratio, saves countless hours and dollars, and may even save […]
Introduction to Cribl with Nick Heudecker
Cribl’s mission is to unlock the value of all observability data – the logs, events, metrics, and traces comprising your monitoring and security environment. This session provides an introduction to Cribl’s approach to restore choice and control over observability data with Cribl Stream, its leading observability pipeline. We’ll also explore Cribl Edge and the newly […]
Swimlane Good (SecOps) Defense is Having a Good Offense
Every security organization, team, and individual is trying to get ahead of everything on their plate but seldom do we have the time to do everything we need to get to everything. Many teams have immense backlogs of processes, activities, and programs that, given enough manpower, would help reduce the risk to their organization. In […]
Doing Security Incident Response in Your Sleep with Swimlane
As we all know, security operations is an around-the-clock job, but building automation response systems is a way to drastically reduce the impact of a potential breach, as well as human error and much of the fatigue that teams are plagued with daily. In this section, we will show you how to measure your readiness […]
Building a SecOps Automation Foundation with Swimlane
The SecOps Automation Maturity Model is a framework for helping organizations better understand where they are on the security automation maturity spectrum. In this section, we will discuss and demonstrate what both a foundational and enriched SecOps automation state should look like and how to better measure and prepare your team for an automation journey.
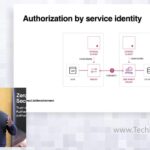
HashiCorp Zero Trust Security Overview
HashiCorp provides infrastructure automation software for multi-cloud environments, enabling enterprises to unlock a common cloud operating model to provision, secure, connect, and run any application on any infrastructure. In this presentation, Megan LaFlamme, Director, Product Marketing, will introduce HashiCorp’s approach to zero trust security with identity-based access and authorization.
Micron Secure Device Configuration Demo using Triathlon Platform
One of the Achilles’ heels of the cybersecurity industry is that the establishing of trust has always been expensive, complex, and untimely. Semiconductors have a fragmentation problem, creating challenges for embedded security experts. Meanwhile, cloud platforms want to speak a single API language that is hardware agnostic. But there has been no strong ecosystem force […]
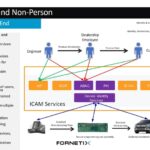
Micron Device Identities on ICAM – IT Meets OT
Identity, Credential and Access Management is a foundational component of building trust. Building trust starts with determining identity, and, from there, continuing to build trust with authentication and authorization. In the supply chain it also starts with identification, authentication, and authorization. Considering how products come to market, the ability to securely communicate is based on […]
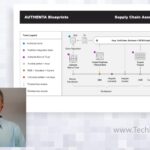
Micron Authenta Customer Blueprints
Authenta Cloud Platform customers are some of the industry’s most pioneering companies pushing forward the next generation of connected products and services at the edge. This ranges from the data centers lowering operation costs and deploying innovative business models, like Bare-Metal-as-a-Service, to the auto OEMs supporting Mobility-as-a-Service trends. All of these use cases require foundational […]
Micron Silicon Trust in the Subscription Economy
Customers are no longer satisfied with static product ownership as we lean into the subscription economy. The digital transformation is forcing every industry to build products that can evolve, giving them access to dynamic revenue streams, but this introduces new manufacturing and cybersecurity gaps that are hard for most companies to deal with. Micron has […]
How to Use FortiCNP, Fortinet’s Cloud-Native Application Protection Platform, to Help Manage Cloud Risk
FortiCNP is Fortinet’s cloud-native application protection platform (CNAPP) that simplifies cloud security operations through native integrations with Cloud Service Providers’ security services and Fortinet Security Fabric solutions to provide unified and contextualized risk visibility across cloud resources and cloud environments. FortiCNP provides resource risk prioritization and scalable workflows to help security teams prioritize risk management […]
How to use FortiDeceptor – Fortinet’s Deception Technology, to Help Protect OT and IT Networks
FortiDeceptor, Fortinet’s innovative, non-intrusive, agentless OT/IT/IoT deception solution is a force multiplier to current security defenses, providing early detection and response to active in-network threats. The FortiDeceptor decoys generate high-fidelity, intelligence-based alerts that result in an automated incident response to help stop zero-day attacks. In this session, VP Product Management, FortiDeceptor, Moshe Ben Simon, provides valuable […]
How to use FortiRecon – Fortinet’s Digital Risk Protection service, to Help Detect, Prevent, and Respond to External Threats
FortiRecon provides organization-specific, expert-curated and actionable External Attack Surface (EASM) intelligence, identifies threat actors’ activity and brand infringement, and monitors ransomware data leaks, to proactively help remediate and execute takedowns or purchase the stolen data on an organization’s behalf. In this session, SVP Product Technology & Solutions, Carl Windsor, introduces FortiRecon, Fortinet’ Digital Risk Protection (DRP) service, […]
ZPE Demonstrates Network Automation Blueprint to Recover a Failed FortiGate Upgrade
Rene Neumann demonstrates how ZPE Systems Netbox Network Automation Blueprint can help recover a failed FortiGate firewall upgrade. After introducing the environment for the demo, Rene shows how Netbox can be used as a source of truth to easily keep data current, update Nodegrid details, and update device details using a console connection. He then […]
Expanding the QLC Opportunity with 4th Generation Solidigm QLC SSDs
As data sets grow, the need for more efficient and higher capacity storage is imperative. Learn how Solidigm is planning to address higher capacity, higher performance and greater overall efficiency with the current and future QLC SSDs. Presented by Yuyang Sun, Senior Product Marketing Manager for QLC Products at Solidigm, this presentation discusses the evolution […]
Solidigm QLC SSD Customer Value Stories
QLC NAND SSDs are being adopted in both cloud and enterprise across a range of workloads. This presentation by Charles Anyimi of Solidigm provides an in-depth overview of how customers are addressing significant storage challenges through the implementation of QLC SSDs. By presenting multiple case studies, Anyimi illustrates the operational efficiencies and cost savings that […]