Ventev A Look Inside – Wi-Fi 6E and Aesthetic
Those in our industry havbe been keeping an eye on Wi-Fi 6E, as well as the rise of inconspicuous Wi-Fi. We know huge benefits come with Wi-Fi 6E, but what’s taking so long? What are some of the latest discreet Wi-Fi technologies out there? Tune in to Dennis Burrell’s session to get a closer look […]
Hanging Tough in Rough Conditions with Ventev
Safeguard network infrastructures from exposures to extreme conditions in your initial planning to avoid costly and severe consequences. Ventev works closely with our strategic partners to ensure our solutions are optimized with their technologies and protect them from the elements. Join Jared VanAllen on how to be tough when it’s rough out there.
Ventev Network and Wireless Deployments for Challenging Environments
Keeping a wireless network up and running is critical in today’s digital world. Combine that with harsh environments and state’s mandates and you have a flurry of obstacles to overcome. In this session, Rodger Hyle will cover the various challenges with wireless deployments, and the solutions to connect, protect, and enable our wireless world.
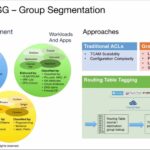
Arista Cognitive Campus Architecture
A look beyond Wi-Fi on how Arista is exploiting it s expertise in the wired side of the house to make Wi-Fi management better. Arista’s dedication to standards and use of standardized VxLAN to provide traffic aggregation to replace controllers; extending MSS-G traffic from Wi-Fi devices and the improvements we are adding to the switching […]
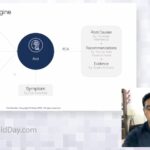
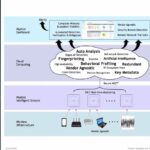
Arista AI and ML Driven Network Assurance
A view into Arista’s Cognitive Campus evolution as we move towards using NetDL (Network Data Lake) that aggregates data from multiple sources in the network and its environment, NetDL helps create the machine learning models and the intelligence required provide to tools required by Network administrators to ensure an excellent experience for their Wi-Fi users. […]
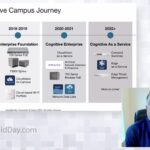
Arista Cognitive Campus Introduction and Vision
In this presentation, see an introduction of Arista’s Cognitive Campus, history and the way forward Arista’s priorities and how Arista is rethinking the enterprise mobility architecture with data driven approach and an unwavering dedication to quality.
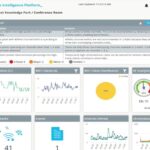
Wyebot Product Demo – Autonomic Wi-Fi, Network Tests, Device Forensics, Historical PCAPs, REST API, SAML Support
The Wyebot solution consists of two components: Cloud-enabled SaaS Application and IoT Sensor with edge computing. The solution utilizes network behavioral profiling, sophisticated wireless algorithms, and advanced wireless optimization capabilities, to deliver 24×7 reliability and peak performance for enterprise WiFi networks. The Cloud-enabled architecture, coupled with distributed processing on the IoT Sensor provides a highly […]
Wyebot System Architecture – Unique Dedicated Multi-Radio WiFi Sensor Solution With Built-in Spectrum Analysis
The Wyebot solution consists of two components: Cloud-enabled SaaS Application and IoT Sensor with edge computing. The solution utilizes network behavioral profiling, sophisticated wireless algorithms, and advanced wireless optimization capabilities, to deliver 24×7 reliability and peak performance for enterprise WiFi networks. The Cloud-enabled architecture, coupled with distributed processing on the IoT Sensor provides a highly […]
Wyebot Company Intro – Game-Changing Simplicity of Deployment
Wyebot’s mission is to lead the Optimization of the Mobile Enterprise. The enterprise WiFi network has migrated from a convenience to business/mission critical (Manufacturing Automation, Telehealth, eLearning for Education, Point-of-Sale in Retail) while at the same time increasing in complexity due to the explosion of IoT devices, limited IT resources, remote travel challenges and rapid standards evolution. IT organizations need […]
Scaling IaC Collaboration with RackN Breaks IT Silos
RackN breaks DevOps silos with collaboration focused IaC with the Digital Rebar platform. Enable GitOps and self-service by using integrated labs and versioned, composable and reusable automation. Presented by Rob Hirschfeld, CEO & Co-Founder, and Shane Gibson, Chief Solutions Architect and Founding Member, RackN. Visit rackn.com/products/infrastructure-as-code/ for more information.
Scaling Ansible Day 1 and 2 Operations with RackN
RackN orchestrates Day 2 operations with Digital Rebar IaC platform. Our ability to switch tools like Ansible between workflows and work orders allows platform teams to create portable automation for all infrastructure types. Presented by Rob Hirschfeld, CEO & Co-Founder, and Shane Gibson, Chief Solutions Architect and Founding Member, RackN. Visit rackn.com/products/provisioning-automation/ for more information.
Scaling Terraform Day 1 and 2 Operations with RackN
Explore how RackN architected the Digital Rebar IaC platform so platform teams can seamlessly scale tools like Terraform to across multiple teams, cloud, and infrastructures. Presented by Rob Hirschfeld, CEO & Co-Founder, and Shane Gibson, Chief Solutions Architect and Founding Member, RackN. Visit rackn.com/products/provisioning-automation/ for more information.
RackN Enterprise Scale Infrastructure as Code
RackN Digital Rebar helps companies scale Infrastructure as Code with our full life-cycle distributed IaC platform. Learn about how RackN addresses the challenge of tools silo to create integrated infrastructure pipelines for Enterprises. Presented by Rob Hirschfeld, CEO & Co-Founder, RackN Visit rackn.com for more information.