Threat hunting has become quite mainstream over the past several years, but what is it and should your organization be doing it? In this session, Cisco dives into threat hunting as a concept, explores real world findings and the concepts of threat hunting. You’ll also see a few lessons learned from building a global platform, […]
Search Results for: 1D0-724 Exam Labs 🍳 1D0-724 Valid Dumps Questions 💻 1D0-724 Reliable Mock Test 🍎 Open website { www.pdfvce.com } and search for ▷ 1D0-724 ◁ for free download 💄Reliable 1D0-724 Real Exam
Advanced Analytic Alerting From Flow Analysis with Riverbed NetProfiler and ASM
Gwen Blum, Senior Technical Evangelist, presents actionable advanced analytics for remote workers using Riverbed NetProfiler and ASM. He demonstrates these products in real time using Riverbed tools deployed in Microsoft Azure as well as cookbooks in the Riverbed Community Toolkit.
Automating Day 1 to Day N Operations with NodeWeaver
We continue the “hero’s journey” to focus on addressing the real world operational challenges from day 1 going forward. Here we will discuss and demonstrate cluster expansion, failover, automated management, autoscaling, remote management, application deployment, and service chaining. We will also discuss the unique security challenges presented by the distributed edge and how NodeWeaver addresses […]
Using Swimlane Low-Code Security Automation to Solve Cross-Departmental Security Use Cases
This real-world use case highlights how a Swimlane Fortune 500 financial services customer matured its implementation of low-code security automation beyond common SOAR use cases and the SOC. Swimlane’s Bryon Page (Director Solutions Architecture) and Cody Cornell (Co-founder and Chief Security Officer) showcase how Swimlane is used across departments to build workflows that update security […]
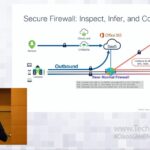
Cisco Secure Firewall 3100
This session showcases hardware and software innovations around Cisco Secure Firewall 3100 Series appliances. It covers such topics as resilience and scale, multi-tenancy, encrypted traffic handling, and application of AI/ML technology to near-real-time application and threat detection.
Mist Systems AI-driven RRM with Bob Friday and Sudheer Matta
Bob Friday, Co-Founder and CTO, and Sudheer Matta, VP Product, show off a new feature for Wi-Fi assurance: AI-driven Radio Resource Management (RRM). They demo how it adapts in real-time to changing RF characteristics, and how service levels are used to demonstrate the impact that AI-driven RRM has on the user experience
Aruba AI-Powered Network Operations
“It must be your network”! If you’re a network admin, then you must be pretty used to others pointing fingers at the network for client and application issues, when the real culprit was outside the network. How often have you found yourselves scrambling to prove your innocence to reduce the MTTI (Mean Time To Innocence)? […]
DriveScale Demo
Chris Unkel, Distinguished Engineer at DriveScale, demonstrates the key steps in orchestrating and automating composable infrastructure via the DriveScale Composer, along with real-life examples of Cassandra and Kubernetes deployments.
Scaling Up with AI and Network Observability: cPacket’s Technological Leap
cPacket is using AI and network observability to help manage and improve networks more effectively. Their AI algorithm can quickly analyze lots of network data in real-time to find patterns and problems that might be missed with manual monitoring. cPacket’s solutions work across different types of networks, like physical or virtualized ones, to help operators keep track of performance and security. Read more in Jeffrey Powers’ recent LinkedIn Pulse article following Networking Field Day 35.
Enabling Performance and Capacity Scaling for Big Data Using Intel Cloud Storage Accelerate Layer (CSAL)
Cloud service providers are pushing the boundaries of storage capacities to meet the performance requirements of big data workloads and expanding data volumes. Intel and AliCloud collaborated on Cloud Storage Acceleration Layer (CSAL) to address NAND density and scale challenges. CSAL uses Intel Optane SSDs to improve system performance while reducing costs scaling QLC NAND […]
TSecond Throws AI Brycks at the Edge at EFD3
Mark Houtz recently attended the Tsecond presentation at Edge Field Day 3 focusing on their application of AI at the edge. In this article he discussed the complexities and challenges of deploying robust AI technologies in edge environments but highlighted how TSecond’s new solutions are effectively addressing these issues. Houtz’s article underscores the potential of edge AI to transform data processing and analytics in real-time applications, setting a new benchmark in the industry.
Deploy AI Everywhere From Edge to Data Center and Cloud with Intel
In this session, Ronak Shah, AI Product Director at Intel’s Data Center and AI Group, reflects on the full day of presentations at AI Field Day 4. In addition to Intel, the day included representatives from Nature Fresh Farms, VMware by Broadcom, Google Cloud, and Kamiwaza. He emphasizes the prevalence of AI deployments, particularly inferencing […]
Solo.io Loop and Squash for Application Observability and Resilience
Ensuring the resilience and failure tolerance of cloud-native applications require visibility into systems that are fundamentally distributed. We will show how the Service Mesh Hub allows us to extend any underlying service mesh in order to provide a myriad of tools for maintaining the application health. from monitoring and tracing to chaos engineering. We will […]
ExtraHop Product Demo: Live Attack Scenario
In this session, Jeff will simulate a Red vs Blue exercise using Reveal(x) from ExtraHop to hunt a threat actor through the attack lifecycle. Based on over 20 years of experience as a coder, architect, and leader of multiple security domain teams, Jeff will showcase the Reveal(x) product by playing through a threat detection scenario […]
Building High Performance, Efficient Content Delivery Network Nodes with Intel Optane
Intel technologies, including Optane and NAND storage devices, are enabling new architectures and expanding memory and storage tiers. Join us as we share real-life examples, some focused on expanding memory capacity, while others show that implementing an ultra-fast storage tier can drive performance acceleration. In this video, Nash Kleppan delve into CDN workloads.
Deliver High IT performance with Cisco Nexus Insights and Assurance
Cisco Nexus Dashboard Insights gives customers the ability to monitor and analyze their network in real time to identify anomalies, to provide root-cause analysis and capacity planning, and to accelerate troubleshooting. In this sessoin, you’ll learn ny tracking historical context, collecting and processing hardware and software telemetry data, and correlating customer designs with Cisco best-practices, […]
Defending Web Applications Against Advanced Threats with Fortinet Machine Learning
Applications are more dynamic and are delivered faster than ever. Web Application Firewalls (WAFs) have traditionally provided application protection with strictly static approaches. These static approaches haven’t been able to keep up with the continuous improvements of quickly iterating applications. Watch as Fortinet demonstrates real-world attack scenarios exploring anomalous traffic, bot attacks, and API security […]
Economic and Operational Advantages of Cloud DRaaS with JetStream Software
Disaster Recovery (DR, or sometimes BC/DR) in the cloud can be more economical than legacy on-premises DR. JetStream Software’s Rich Petersen shows how storing recovery data and metadata in object storage and provisioning cloud-based compute nodes dynamically when needed can reduce the cost of DR infrastructure by 50% to 60%, making cloud a game-changer for […]
Illumio Segmentation Has Nothing To Do With Vulnerability Management
Myth III: Segmentation has nothing to do with vulnerability management. Vulnerabilities are inevitable and they must be patched. BUSTED: See how overlaying vulnerability information on a real-time application dependency map helps visualize and quantify risk and prioritize patching decisions. When patching isn’t an option, use segmentation as a compensating control to minimize risk.